Parsing MITRE ATT&CK CTI for Threat Emulation TTPs
When planning for purple team assessments and for threat emulation assessments, it’s valuable to compile the relevant Tactics, Techniques, and Procedures (TTPs).
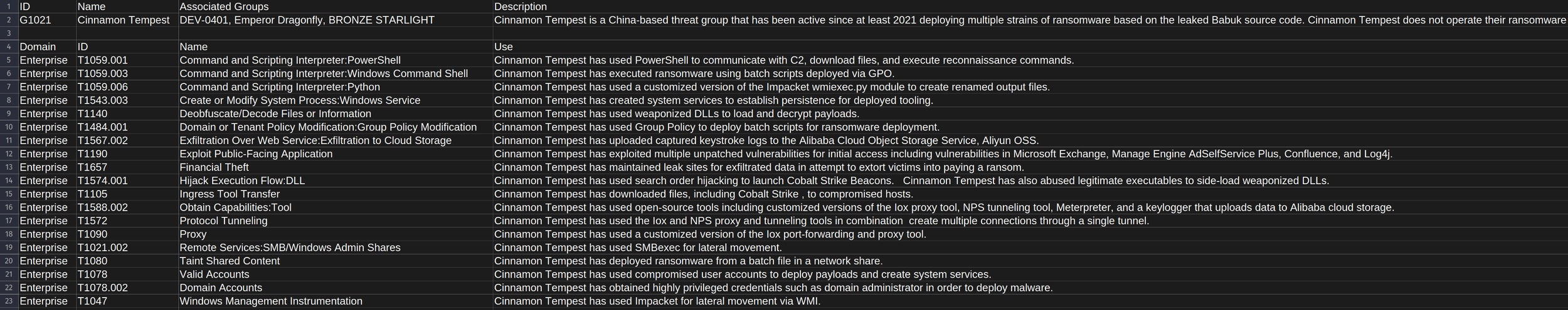
Borasec has written a simple python scraper to help with this part of the planning process. The script parses the Cyber Threat Intelligence content hosted by MITRE, for the desired keywords for information on the matching threats. Optionally, each threat returned can be expanded to return it’s associated TTPs, as well as output to both CSV and to JSON for consumption with other tooling.
The python script is available on github: https://github.com/borasec/mitre_cti_parse
Listing all the available options, the search term for the desired threat is mandatory, as is one of the categories actor “Group”, malicious “Software”, or executed “Campaigns”. Digging deeper to return associated TTPs, as well as file outputs are optional arguments.
Searching actor groups for keyword "dragon".
Results for the Conti Ransomware software, with csv and json file output arguments.
CSV file opened showing exported information for "Cinnamon Tempest".